We have built a Security Operations Center at Netskope in short order. Facing the vast expanse of the Security Operations ocean, I grabbed my board with my team and focused on doing a few things really well. We documented workflows, expanded our visibility, and tuned monitoring systems. We paddled out from shore, braving the shark-infested waters of the threat landscape. Of course, with many tools comes many threat data sources, and as expected, the threat data ingestion tidal wave quickly manifested itself.
Testing the waters
Our SOC, like most, operates in an extremely fast-moving environment with shiny objects everywhere. We are constantly asked to look at the latest technology, most of which are just little swells that won’t become waves and aren’t worth the energy to surf. I am always interested in checking out new technology to understand the potential fit. But if you can’t explain the use case to me in 30 minutes, I move on. I surf big waves. This is a story of a swell that quickly turned into a big wave for my team.
A big wave
When approaching the topic of orchestrating static indicators of compromise such as hashes, IP addresses, and domains, I was introduced to an in-house solution: Cloud Threat Exchange (CTE). CTE is a module that runs in a lightweight collection of Docker applications, named Cloud Exchange, that ingests, manages, and shares IP addresses, domains, and file hashes. It’s free, too.
My team and I pushed up from our boards. After careful research of our own environment and prioritizing the many threat data routing options available to us, we deployed our own instance in the SOC and started connecting key data points.
Hanging ten
We are now routing high-fidelity threat data multi-directionally and in near-real-time between our Netskope instance and other monitoring points, such as EDR and our email gateway. Furthermore, we are channeling certain output for incorporation into the Netskope threat detection engine. We are up on our boards and carving a ride on the wave.
We are not drowning. We are routing threat data faster than ever and you can too. We are up on our boards and can see the threats below the surface sooner. This protects Netskope AND drives improvements in our own threat detection engine to protect our customers.
How it works
Sharing threat intelligence is configurable between any two connected systems. For instance, we can facilitate sharing between different endpoint providers or even multiple Netskope cloud tenants. As threat intelligence and IOCs are received via CTE, we can enforce real-time security enforcement, blocking user access to malicious sites or files that can endanger our security posture. The possibilities are truly mind-boggling.
Consider this diagram an example of how we think about using CTE for automated indicator routing in the SOC:
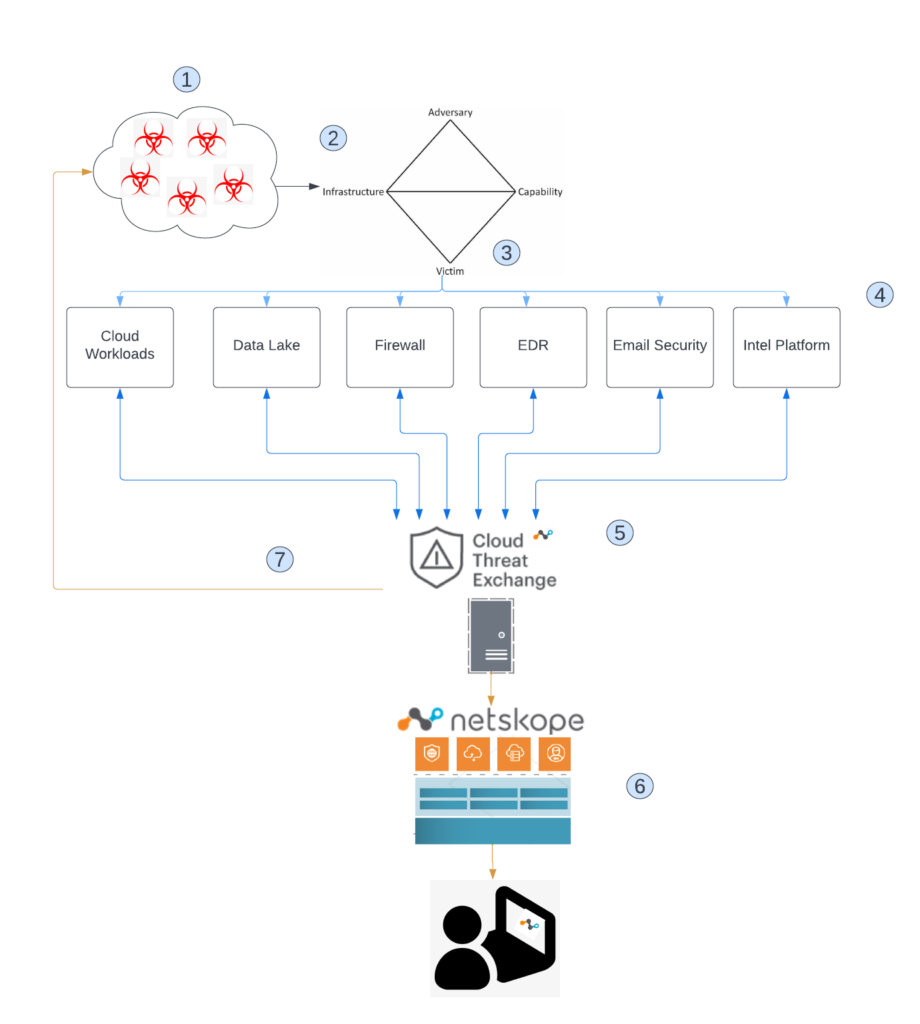
- The industry and community channels have an enormous amount of threat data to sift through. Sharing is caring, but is it useful?
- To make threat data useful, organizations should analyze the threat using various analysis techniques. Intelligence analysis is outside the scope of this post, but for the purpose of this example, we will assume that the threat data that is feeding your security instrumentation is of high fidelity and vetted through rigorous intelligence analysis.
- As indicators are fed to security instrumentation, such as EDR, email gateways, and firewalls, certain actions are constantly performed depending on numerous configuration and environmental factors. Again, those tuning considerations are outside the scope of this post, but for the purpose of this example, we will assume that your tools are tuned and working as expected.
- Depending on the partnership connections in place at any given time, every piece of your security stack may or may not be capable of integrating with each other. Chances are, there will be some tool that cannot talk to another.
- This is where the power of CTE comes in. There are several out-of-the-box integrations, such as CrowdStrike Falcon, VMware Carbon Black Cloud, SentinelOne, and ServiceNow. In addition, we add our own plug-ins to enable sharing between CTE and our own IT systems and/or scripts.
- Of course, our own Netskope security stack benefits from the near-real-time ingestion of the routed threat data. The client pulls the updated rules from the Netskope Security Cloud and the user and data are protected.
- Since sharing is caring, we can now share indicators out to wherever we choose, be it our own internal intelligence hub, or external partner organizations.
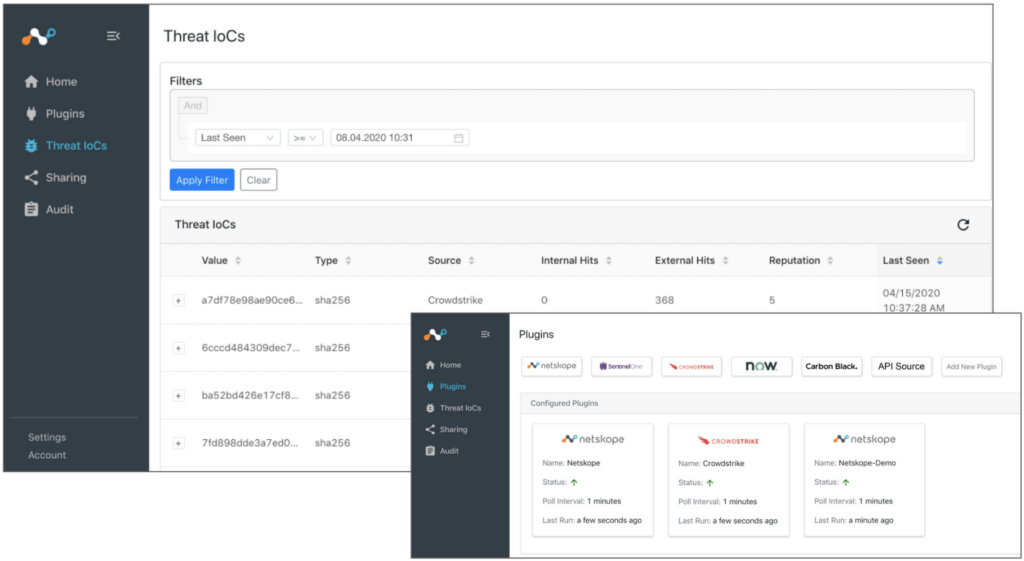
Dashboard
The CTE dashboard provides information on how frequently IOCs have been seen and from what systems, enabling customers to determine the scope of an attack surface. We can also configure when IOCs are timed-out due to staleness, plus choose which IOC sources to trust when they are provided with conflicting (e.g. ‘safe’ versus ‘suspicious’) information. This allows for granular control and decisions on which indicators should be routed where, and for how long.
Ready for more waves (wash, rinse, repeat)
For our SOC, CTE enables even more robust automation and orchestration capabilities to gain full visibility into every event that is happening here. For example, we can make a secondary call to add to monitoring for a priority use case. We have fewer false positives because we are considering more data points more thoughtfully. Pervasive attacks and their IOCs can trigger IR workflows or orchestration playbooks to automate response steps. This makes our security analysts more efficient across multiple security tools. As the SOC continues to evolve with the business, thoughtful implementation of technologies such as CTE provide a much-needed mechanism for us to keep our heads above water and see what lurks beneath the surface.
Ready to use CTE?
There is no charge to use CTE or any of the modules running on Cloud Exchange. CE is a business development tool provided at no charge to Netskope customers and covered by the Netskope EULA. You can download it from Netskope’s public Github repository once you are ready to start surfing! Please contact your Netskope account team or [email protected] if you have any questions.




 Back
Back 





















 Read the blog
Read the blog